5G-Sierra
Realize secure 5G infrastructures for resilient production systems and facilities through a comprehensive toolbox encompassing methods to prevent, detect, and respond to attacks on industrial 5G networks.
5G in Industrial Networks
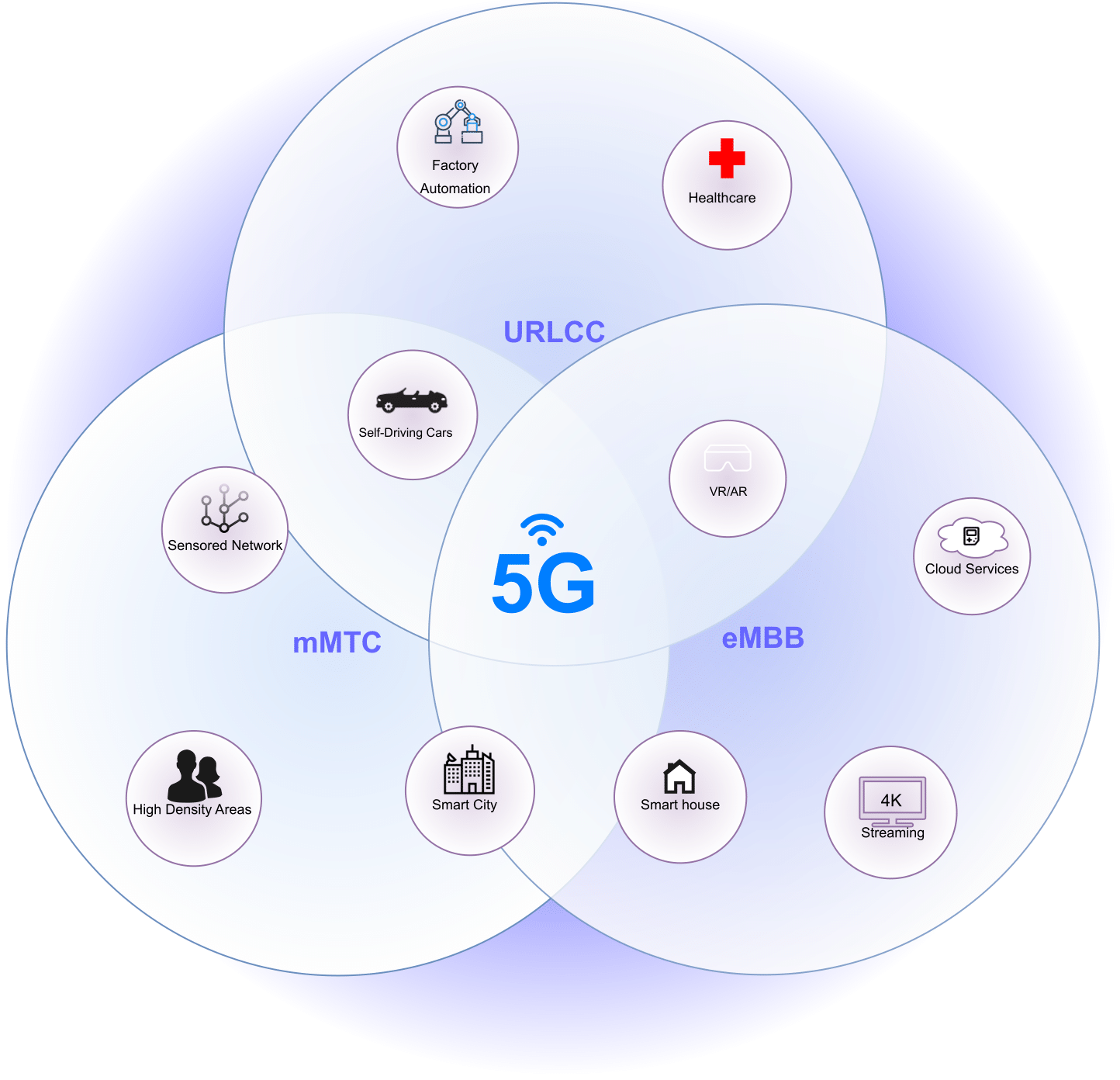
5G is the latest version of mobile networks. Its unique features make it versatile for different real-life situations. As sown in the Figure, Enhanced Mobile Broadband (eMBB) provides fast download and upload speeds, Massive Machine Type Communication (mMTC) enables 5G to connect numerous devices, and Ultra-Reliable Low-Latency Communication (URLLC) ensures reliable communication with minimal delay. URLLC is particularly well-suited for industrial applications due to its ability to meet the fundamental requirements of industrial communication: reliability and low latency. More specifically, 5G is anticipated to enhance process functions like real-time remote maintenance and monitoring, while also enabling connectivity for numerous sensors in the upcoming Industrial Internet of Things (IIoT).
However, the integration of 5G into the communication infrastructure of industrial networks expands the attack surface of these networks. This is due to the introduction of new attacks related to wireless networks, specifically targeting 5G, which were not existent in industrial networks before. Some significant examples of these threats include exposure to jamming attacks, inadequate security of the wireless interface, and insecure/insufficient authentication mechanisms. For a comprehensive list of 5G-related threats, please refer to the report published by the European Union Agency for Cyber Security (ENISA). The 5G Sierra project brings together academia and industry to create a secure 5G infrastructure for industrial networks. Its main objective is to develop solutions to detect, prevent and response to attacks.
Our Solution
To establish a secure 5G infrastructure, 5G-Sierra will offer a comprehensive toolbox encompassing: (1) Robust authentication, authenticity, and redundancy methods for attack prevention, (2) Mechanisms for detecting anomalies and jamming and, (3) Solutions to address potential attacks, including device exclusion and accountability controls. The 5G-Sierra secure infrastructure is shown in the figure below.
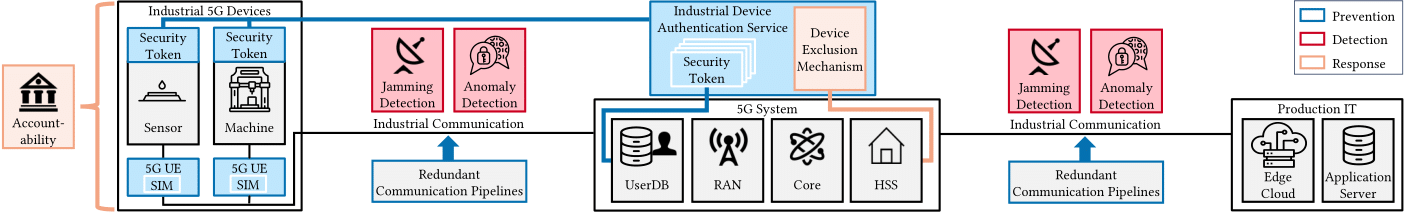
Prevention
To enhance security and prevent attacks, an Industrial Device Authentication (IDA) service is in development. It will rely on hardware security tokens to store critical security data such as keys and certificates. The IDA’s core function is to consistently verify the identity of industrial devices and set up symmetric keys for secure communication between devices. Additionally, for safeguarding Time Sensitive Networking (TSN) data, including synchronization and scheduling packets, the project is implementing the MACsec protocol, and redundant communication channels are being established to ensure its transmission.
Detection
We will employ two security methods to detect attacks. Firstly, we are developing an IDS system tailored specifically for 5G wireless communication. This system will continuously monitor the traffic on the wireless connection. Secondly, we have implemented an SDR-Jamming detector. This two-pronged approach aims to provide robust protection for the wireless interface. The jammer detector is designed to identify signal disruption attacks, and any attacks that go unnoticed by it are expected to be detected by the IDS through the observation of packet drops or delays.
Additionally, it’s crucial to highlight that the IDS has the capability to identify most attacks that disrupt the expected functioning of the industrial network. The rationale behind the IDS lies in the deterministic nature of industrial networks, where the same control loops occur at standardized intervals. We leverage this inherent characteristic and integrate features of the wireless interface to detect potential attacks.
Response
Sierra’s 5G implementation will incorporate two controls to respond to attacks: firstly, a PKI-based approach to address the issue of unverified industrial device authenticity, and secondly, a 5G-based method to block SIM cards in the event of malicious activities. The PKI-based response includes actions like suspending or revoking certificates, with a requirement for certificate validation through the Online Certificate Status Protocol (OCSP) responder for secure communication. Meanwhile, the 5G-based response centers on blocking the SIM card associated with the unauthenticated industrial device.
Partners and Fund

This project is funded by the German Federal Ministry for Information Security (BSI) under project funding reference number 01MO23016D. To see the full list of involved parties, click the buttons below.
- oculavis GmbH, Aachen
- Fraunhofer Institute for Production Technology IPT, Aachen
- Swissbit Germany AG, Berlin
- UTIMACO IS GmbH, Aachen
- Keysight Technologies Germany GmbH
- MARPOSS Monitoring Solutions GmbH, Egestorf
- Fraunhofer Institute for Production Technology, Aachen
- Ericsson GmbH, Herzogenrath
- Reusch Rechtsanwaltsgesellschaft mbH